
Hackers Don’t Sleep: Why Your Business Can’t Skip On Cybersecurity
Imagine this… You wake up. Your website is down. Your customer data is stolen and your reputation starts to crumble as hackers from across the world broke into your site while you were asleep.
No alarm. No warnings. You never even thought of needing them, so why set them up in the first place?
This is a nightmare.
Worse. A preventable nightmare.
This is a reality for thousands of businesses every year. Now the real question is simple.
Will you be ready when they come for you?

As a digital marketing agency, we’ve seen marketing results fall off a cliff suddenly and gradually due to a client’s site being hacked can snowball into big, expensive problems. We’re talking lost data, shaken customer trust, and even legal trouble.
We have noticed an increase in sophisticated attacks on small businesses, and now a strong password just isn’t enough. As a result, we’ve developed systems that work with our clients to protect them and our marketing campaign results.
While that may sound technical, the good news is that many of these fixes are easy to do. We created this guide like a conversation, packed with real client experiences, easy analogies, and yes, the occasional joke about zombie bots and toaster passwords. Following it can dramatically decrease your chances of being damaged by cyberattacks.
Quick Note Before We Start

Cyber security and business operations might not mix well if you’re not gifted with computers. Asking your existing service providers to implement these solutions may be the best solution.
It’s always important to keep your team updated on all network related changes. If done improperly you can hinder business operations at best or bring down your network at worst temporarily.
Anyways, we’re starting with easy wins—things you can do today, even if your biggest tech flex is getting the Wi-Fi printer to cooperate (and hey, respect).
But further down, you’ll find tools and tips that may need a bit more know-how or help from an IT professional. Each section comes with a difficulty rating and speedometer like the one below so you know what you’re getting into. 
If something is rated 8 out of 10 that does not mean that you cannot do it alone, but that we strongly recommend calling for backup from an expert if you are not that experienced.
And remember: the more secure your system is, the less “convenient” it may feel. Like adding locks to your front door, it’s a bit of a hassle, but way better than dealing with a break-in.
Let’s get started.
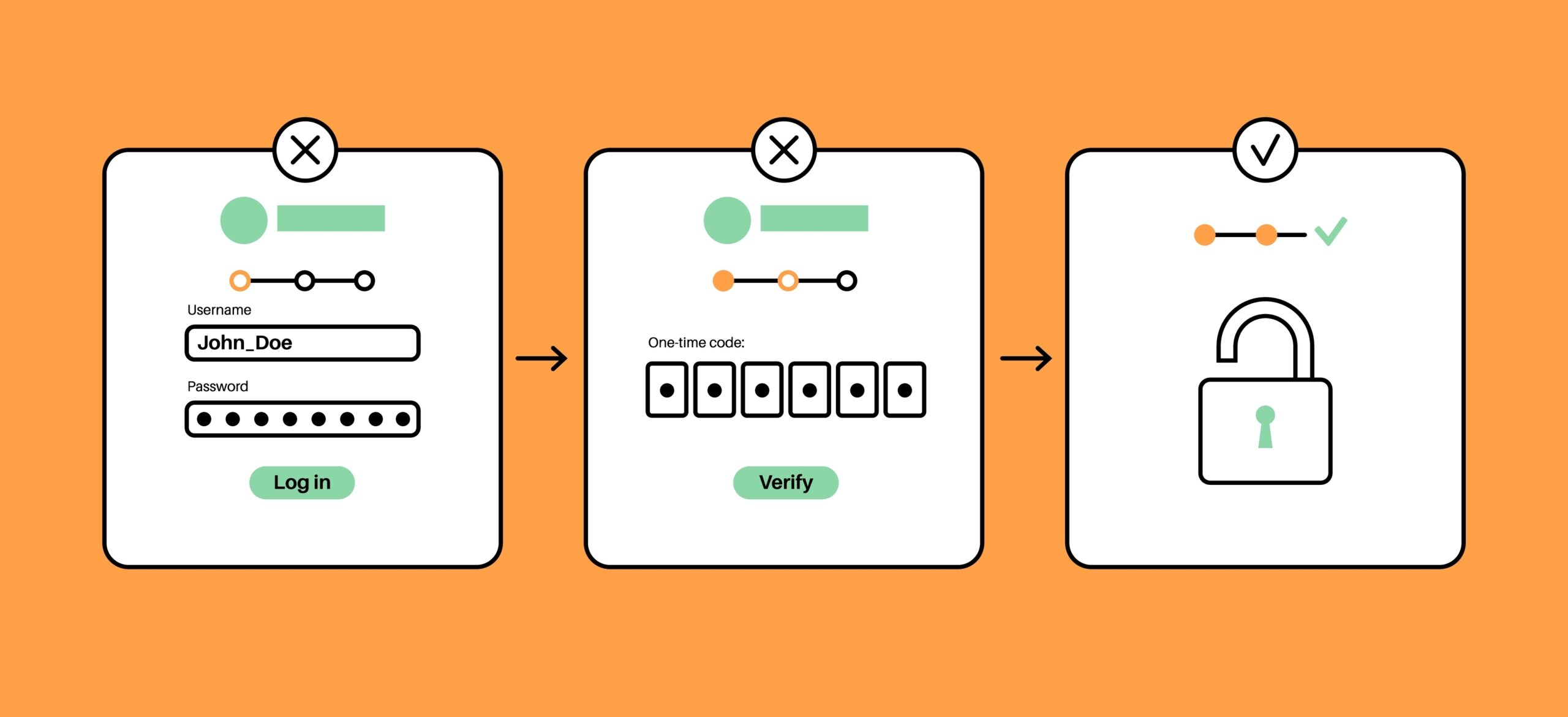
Add Two-Factor Authentication (2FA) To Every Important Account

Difficulty 2/10
“Why do I need a code? Isn’t my password enough?”
Short answer: No.
Think of your password as the key to your house. If someone copies that key, they can walk right in. Two-Factor Authentication (2FA) is the second lock on the door, one only you can unlock.
So even if someone wants to steal your login (trust us, they’ll try), they still can’t get in.
2FA works by requiring two forms of verification instead of just a password. Some platforms use SMS or email, but the safest option is an authenticator app or physical security token. These tools generate short-lived codes that pair with your regular password.
As a business owner, you should enforce 2FA on your entire workforce. You shouldn’t expect everyone on your team to have the company’s cybersecurity front of mind.
The main inconvenience is that some people need to be trained or chased to set it up the first time. But that’s waaayyyy better than losing thousands of dollars to cybercriminals.
Our recommendation is always to set a grace period and lock out those who don’t add 2FA to their account. Remember, they won’t pay for the failures in your systems when there is an incident.
Setting up 2FA is usually quick. Most platforms let you scan a QR code with an app like Google Authenticator or Authy.
Here’s where you should use 2FA immediately:
- Email accounts (especially your business email)
- Cloud storage (Google Drive, Dropbox, iCloud)
- Online banking and accounting tools
- Website logins (especially admin access)
- Social media accounts
If it holds sensitive data or customer access, it needs 2FA. It’s one of the fastest, most effective cybersecurity upgrades you can make.
Without writing a single line of code.
Protect Your Website From DDoS Attacks Before They Take You Offline

Difficulty 4/10
Increases in traffic are great for websites because they can lead to more sales, but if your site blows up 1000x in a night, you are probably being attacked.
A Distributed Denial of Service (DDoS) attack is like thousands of people shoving their way into your store. They pile up, trash the floors, and choke the walls.
Except they aren’t real customers. Just endless waves of bots blocking access, crashing your website, and locking out everyone who actually wanted to visit.
When a website climbs to the top of Google, competitors and bad actors often hit back with DDoS attacks. The worst thing is these attacks don’t come from a single hacker in a hoodie. Instead, they come from a botnet: a network of infected devices around the world, including hacked laptops, smart TVs, and even grandma’s Wi-Fi fridge.
DDoS attacks don’t steal data, but they:
- Crash your website and cost you sales.
- Corrupt internal databases and logins.
- Piss off clients and new customers
- Loss of productivity while your team waits for a fix
Marketing channels like Google and Facebook will continue charging you for traffic even if your site is down due to a DDoS attack. Attackers know this and may use DDoS attacks to slowly degrade your site’s performance, causing users to leave without taking action.
The good news is that you don’t need to be a tech wizard to protect yourself from DDoS attacks.
Here’s what you can do to stay online:
- Host your website with a provider that includes DDoS protection, for example, Wix.
- For existing sites, add content delivery networks (CDNs) with DDoS mitigation like Cloudflare or Sucuri.
- Set uptime alerts so you know the second something goes down.
A CDN makes your site a moving target — attackers can’t hit what they can’t catch. Without one, you are a sitting duck. DDoS attacks are loud, messy, and disruptive, but very preventable when you plan ahead.
Secure Your Login & Website Access From Brute-Force Attacks

Difficulty 6/10
If your login portals are available online, then chances are that they are being tested by bots every day.
While hackers send their bots to brunch and overwhelm your website portals with traffic during a DDoS attack, others aim to test login pages using brute-force attacks (literally guessing passwords). Once they’re in, they can do everything you can… and much worse.
Treating your login page like any other page? Mistake.
It’s the most targeted door on your site. And bots do love to knock.
Unprotected login pages suffer from 2 common types of attacks: Brute force and DDoS. They are easier targets than other pages because CDNs don’t fully protect them.
A bank’s vault is always behind several other locked doors. If it opened from the outside of the building, everyone and their grandmother would want to open it. This is how your publicly visible login pages are operating.

Here’s how to stop them (no PhD required yet!):
Limit the number of login attempts: Just like your phone locks after too many wrong tries, your site should temporarily block users or bots after repeated failed logins. While these may seem a hassle for legitimate users, it’s an easy first step.
Restrict access by IP or Country: If your team logs in from Canada, why allow attempts from North Korea at 3 a.m.? You can restrict access at many levels. If you’re really serious about security, limit access to your office IP address only.
Add a CAPTCHA to your login form: Yes, we know… no one likes picking out blurry traffic lights. But bots like it even less. If you can’t block people from certain pages, you can still ID them like a bouncer before they try to open the door with Recaptcha or Cloudflare.
If you’re on WordPress, tools like Wordfence or Loginizer let you monitor login attempts, add CAPTCHA, block IPs, and much more without writing any code.
Stop Scammers from Pretending to Be Your Boss (Email Spoofing)

Difficulty 3.5/10

Have you ever wired $15k to a scammer because the email said:
Subject: URGENT: Vendor XYZ has changed their payment details, must pay before the end of the day
No? We didn’t either (we swear!).
This is identity theft and email spoofing. And it’s one of the most common, convincing types of cyberattacks in business.
There are two ways hackers pull this off:
- Phishing: They send a fake login page via email. You or a colleague enters the password. Boom: they’re in.
- Spoofing: They imitate someone’s identity without needing a breach, tricking by appearance of the email alone.
Sometimes, it’s as simple as copying a name and swapping out a single letter in the email address (e.g., john@company.com to john@cornpany.com).
The devil is in the details. Our CEO noticed he had received a spoofed invoice email that could have led to a $15k wire transfer. The only red flag apart from a slight email address change? The signature said “Sent from my iPhone”. The accountant who supposedly sent it uses Android. That’s it.
These attacks are designed to hit you when you’re distracted and often come during a busy moment (mid-meeting, Friday afternoon, first thing Monday morning). And because they look real, they slip past filters and common sense.

How to prevent it:
- Train your team to always verify unusual requests by phone or in person
- Flag emails involving money, logins, or urgent actions
- Set internal rules: no financial requests via email only, ever
These scams are subtle, fast, and embarrassing. But they are also preventable with just a bit of awareness.
Here is a simple email template for you to train your team:
Make Sure Your Website Uses HTTPS to Protect User Data
Difficulty 6/10

Would you board a plane that had the words NOT SECURE written on the doorway?
When a site uses HTTPS, that little padlock icon shows the connection is encrypted. This prevents sneaky hackers and cafe shop employees from easily stealing sensitive information, like passwords, messages, or credit card numbers.
The technology behind this is called SSL/TLS (Secure Sockets Layer / Transport Layer Security). It ensures the data traveling between your site and your visitors is sealed.
Encryption is especially important for any site handling sensitive data, but even if you don’t run an online store or collect payments, HTTPS still matters.
Any feature where users share data can be vulnerable without encryption. Without it, anyone on the same network (e.g., a café or airport) can intercept that info. Worse, someone could redirect users to a fake site without them realizing.
Browsers also flag non-HTTPS sites with big warnings. Plus, search engines like Google consider HTTPS a positive ranking factor, giving secure sites a small boost in search results.
“Okay, I get it. But how do I lock it down?”
Most hosting providers sell SSL/TLS certificates, often free through services like “Let’s Encrypt” or bundled with your hosting plan. You just need to install it or activate it. Just make sure your certificate stays up to date.
Important note: even if your site has HTTPS, if an image or script is still loading via regular old HTTP, your browser will cry about it. Tools like whynopadlock.com help you find these issues fast.
If your site still shows “Not Secure,” now’s the time to fix it. It’s a small tweak that doesn’t require major investment or technical knowledge and makes a massive difference in how people interact with your site.
Plugin Vulnerabilities & the Importance of Careful Updates

Difficulty 8.5/10
Here’s something a little more technical: Plugins are great until they’re not.
Not all plugins are created equal. Free plugins can be risky, especially if they’re abandoned – it’s like leaving your back door open. Some site builders, like Wix, are better with plugin security (but pricier), while others, like WordPress, are a plugin minefield (don’t worry, it’s fixable).
With every plugin comes great responsibility new code to your site, and every line of code is a new opportunity for unwanted intruders to poke around.
“But what can go wrong?”

A lot. Especially if you:
- Use outdated or abandoned plugins
- Install from shady sources
- Ignore update notifications
- Stack plugins like they’re baseball cards
Hackers don’t only attack your site directly, they go after the plugin with a known vulnerability. It’s like leaving a window open when the front door is locked.
A marketing client had 30+ plugins. Twelve were outdated. Their homepage got redirected to an online casino, and it took weeks to detect since it was only visible if you were outside of Canada.
Here’s how to avoid that mess:
- Keep it lean: If you’re not using it, lose it. Fewer plugins equals fewer opportunities for failure.
- Update regularly (but carefully): Updating a plugin can sometimes break your site. Always back up first. Whenever possible, use a staging environment or consult your developer before changing live plugins.
- Vet before you install: Check for update frequency (is it still maintained?), number of installs, reviews, and support activity.
- Use tools that watch your back: Services like Patchstack or WPScan monitor known vulnerabilities and patch them for you.
Plugins are like power tools. They’re useful, but dangerous if left lying around unchecked.
Wrapping It Up

Cybersecurity doesn’t have to be overwhelming. From 2FA to encrypted connections and careful plugin management, protecting your business is all about making smart, manageable moves. We built this guide to help you spot cracks before they turn into costly breaches — because prevention is always cheaper than damage control.
Whether you’re locking down the basics or need help navigating advanced threats, every layer of defense adds up.
At Mrkt360, we offer website hardening and standalone cybersecurity systems for businesses that want to take security seriously. For more advanced needs, our expert IT partners are ready to consult and implement the right solutions for your business. Tailored, tested, and built to last.
If you’re ready to take the next step, let’s talk.
